
Optimized Network Intelligence
Aggregate, filter, and optimize traffic from on-premises to hybrid multi-cloud environments before delivering it to security tools—improving detection accuracy and reducing noise.


Deliver clean, high-signal traffic to security tools to improve detection and reduce noise.
Aviz Deep Network Observability aggregates, filters, and enriches traffic across on-prem, edge, and cloud environments—strengthening security posture without replacing existing investments.
Security architectures were designed for perimeter-centric threats and static infrastructure. Modern environments are fundamentally different—and far harder to secure.
Security and operations teams continue to struggle with limited visibility into internal traffic and east–west communication, increasing detection blind spots, and slowing investigation and response in distributed and hybrid environments.
Gartner notes
Without an aggregation and optimization layer, security teams face blind spots where real threats hide among excessive noise.

Aggregate, filter, and optimize traffic from on-premises to hybrid multi-cloud environments before delivering it to security tools—improving detection accuracy and reducing noise.

Expose workload-to-workload traffic across data center and cloud environments to detect lateral movement that perimeter-based tools often miss.

Reduce processing, ingestion, and licensing overhead by optimizing traffic before it reaches IDS, NDR, and SIEM platforms.

Provide enriched, normalized telemetry from across the environment as a single source of truth for AI-assisted investigation and correlation using Network Copilot™.
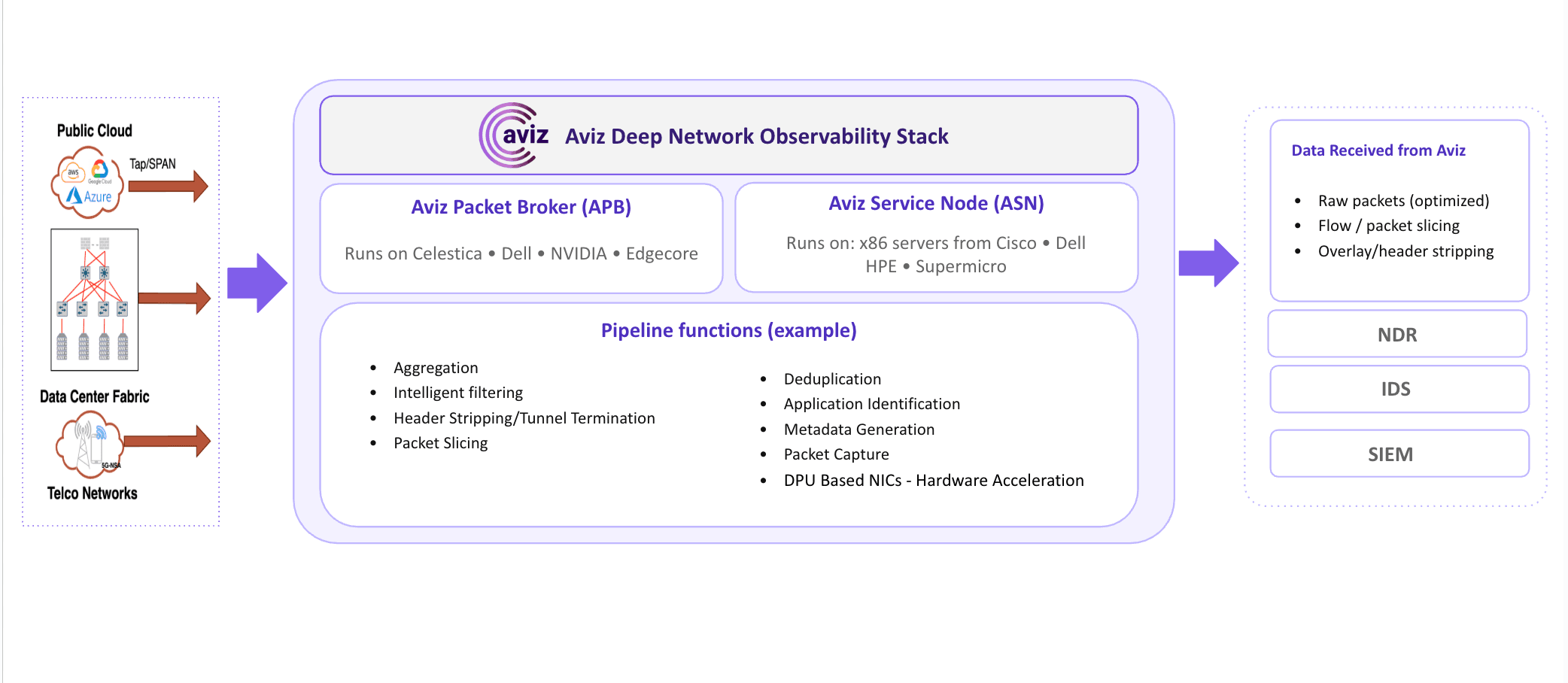
Aggregate and optimize traffic across distributed environments to deliver clean, high-signal data to IDS, NDR, and SIEM platforms—improving detection accuracy and reducing false positives.
Expose east–west traffic patterns and workload-to-workload communication that perimeter-based tools miss, enabling faster detection of internal threats and lateral movement.
Filter, deduplicate, and optimize traffic before it reaches security tools—reducing processing overhead, ingestion costs, and licensing requirements while improving tool effectiveness.
Correlate enriched network telemetry with security signals using Network Copilot™ to accelerate investigations and reduce mean time to respond (MTTR).
Each component in the Aviz platform is designed to work independently or as part of an integrated solution, giving you the flexibility to modernize at your own pace.
Aggregate traffic from physical networks, virtualized environments, and hybrid multi-cloud deployments to establish a unified security visibility baseline.
Filter traffic using packet brokering software running on multi-vendor hardware, ensuring only security-relevant traffic is forwarded to tools.
Eliminate duplicate flows and enrich traffic with application identity and flow intelligence using Aviz Service Nodes on standard x86 platforms, with optional NVIDIA DPU hardware acceleration for line-rate tunnel stripping and high-throughput processing.
Normalize and distribute optimized telemetry at scale—optionally using the Aviz Elastic Node—while enabling parallel delivery to existing IDS, NDR, SIEM, SOAR, and analytics platforms.
Use Aviz FlowVision to centrally manage traffic policies, observe security posture, and operate the entire observability pipeline.
Use Network Copilot™, Aviz's native private AI assistant, to correlate network-derived intelligence with infrastructure telemetry and security signals—accelerating investigations and response.
Faster detection of lateral and internal threats
Cleaner, higher-signal inputs for IDS, NDR, and SIEM
Shorter investigation and response times
Lower security tool ingestion, processing, and licensing costs
Unified security and visibility from on-premises to hybrid multi-cloud
Aviz Deep Network Observability integrates seamlessly with existing security, observability, and analytics platforms. By aggregating, filtering, and optimizing traffic before delivery, Aviz enhances your current security ecosystem—without forcing replacement or lock-in.
Our experts discuss your requirements and demonstrate how Aviz delivers optimized traffic intelligence for faster threat detection and improved security operations.